Let's be honest: your email is probably the most vulnerable part of your business right now. And if you're running a small business here in Peterborough or anywhere else in New Hampshire, that vulnerability could cost you everything.
Email attacks aren't just happening to big corporations anymore. In fact, small businesses have become the preferred target because cybercriminals know you likely don't have the same security resources as larger companies. The harsh reality? One successful email attack can shut down your business for weeks, drain your bank account, or destroy years of customer trust.
But here's the good news: protecting your business doesn't have to be complicated or expensive. You just need to know what you're up against and take the right steps.
The Email Threats Keeping NH Business Owners Awake at Night
Phishing: The Wolf in Sheep's Clothing
Phishing remains the number one threat to New Hampshire businesses. These aren't the obvious "Nigerian prince" emails anymore. Today's phishing attacks are sophisticated, personalized, and designed to look like they're from someone you trust.
A typical scenario: You receive an urgent email that appears to be from your bank, asking you to verify account information immediately. The email looks legitimate, the website link seems real, but it's all fake. One click, and attackers have access to your business banking.
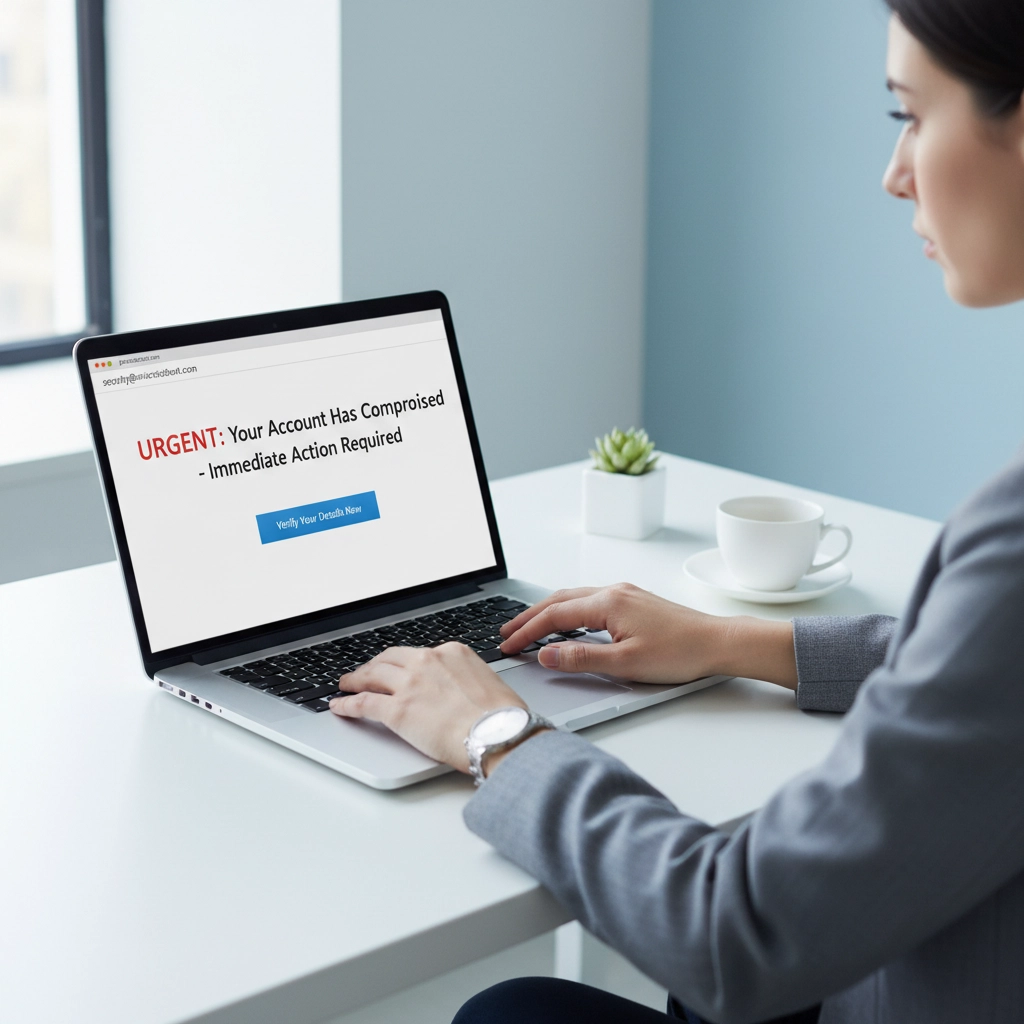
Ransomware: Your Files Held Hostage
Ransomware attacks often start with a simple email attachment. An employee opens what looks like an invoice or important document, and suddenly your entire computer system is locked down. The attackers demand payment: often thousands of dollars: to unlock your files.
Local businesses have been hit hard by these attacks. Some pay the ransom and still don't get their data back. Others lose weeks of productivity trying to recover from backups that may or may not work properly.
Business Email Compromise: The Inside Job That Isn't
This is where attackers gain access to your actual email account and use it to trick employees, customers, or vendors. They might send fake invoices, redirect payments to their accounts, or request sensitive information: all from your legitimate email address.
What's at Stake for Your New Hampshire Business
The numbers don't lie. Small businesses that suffer a successful cyberattack face:
- Average recovery costs of $200,000+
- Weeks or months of operational downtime
- Loss of customer trust and reputation damage
- Potential legal liability under New Hampshire data protection laws
- Regulatory fines and compliance issues
For many small businesses, these costs are simply insurmountable. About 60% of small businesses that suffer a cyberattack go out of business within six months.
Building Your Email Security Defense
Step 1: Train Your Team (Your First Line of Defense)
Your employees are both your biggest vulnerability and your strongest defense. Most successful email attacks succeed because someone on your team made an honest mistake.
Teach your team to recognize red flags:
- Urgent requests for money transfers or sensitive information
- Unexpected attachments, especially from unknown senders
- Emails requesting password changes or account verification
- Messages with spelling errors or awkward phrasing
- Links that don't match the sender's supposed organization
Implement the "pause and verify" rule: When any email creates urgency or pressure, train employees to stop, breathe, and verify through a separate communication channel before taking action.

Step 2: Implement Technical Safeguards
Email Filtering and Anti-Malware Protection
Deploy enterprise-grade email filtering that scans messages before they reach your inbox. This catches most malicious attachments, suspicious links, and known phishing attempts.
Multi-Factor Authentication (MFA)
This is non-negotiable. Even if someone gets your password, MFA provides a second layer of protection. It's like having a deadbolt on your front door: simple but effective.
Email Encryption
For sensitive communications, use encrypted email. This ensures that even if messages are intercepted, they can't be read by unauthorized parties.
Secure Email Authentication
Implement SPF, DKIM, and DMARC protocols. These technical measures verify that emails claiming to be from your domain are actually legitimate.
Step 3: Create Clear Email Policies
Establish written policies covering:
- Acceptable use of company email
- How to handle suspicious messages
- Requirements for password strength and updates
- Procedures for reporting security incidents
- Guidelines for email use on personal devices
Make these policies practical, not intimidating. Your employees need to understand them and actually follow them.
Step 4: Secure Remote Access
With remote work becoming standard, protect employees working from home:
- Require VPN use for accessing company email
- Ensure personal devices have updated antivirus software
- Implement policies for using public Wi-Fi
- Enable automatic screen locks on all devices

Step 5: Backup Everything (Seriously, Everything)
Maintain comprehensive backups of all email data and systems. Test these backups regularly: you don't want to discover they don't work when you need them most.
Keep both online and offline backups. If ransomware hits, offline backups may be your only salvation.
Why Local IT Support Makes All the Difference
Working with a local, certified IT partner like Preferred Computer Solutions offers advantages you simply can't get from remote support or generic solutions:
Immediate Response When It Matters Most
When you're under attack, you need someone who can be on-site within hours, not days. Local IT support means real people who understand your business and can respond immediately.
Understanding of Local Regulations
New Hampshire has specific data protection requirements. Local IT professionals understand these regulations and can ensure your email security measures meet compliance standards.
Personal Relationships and Trust
You're not just another ticket number. Local IT providers build long-term relationships with their clients, understanding your unique needs and challenges.
Ongoing Monitoring and Maintenance
Email security isn't a "set it and forget it" solution. Threats evolve constantly, and your defenses need regular updates and monitoring.
Your Email Security Implementation Roadmap
Week 1: Immediate Actions
- Assess your current email security setup
- Enable multi-factor authentication on all email accounts
- Begin employee training on recognizing phishing attempts
Week 2-4: Build Your Defenses
- Deploy professional email filtering and anti-malware protection
- Establish clear email security policies
- Set up encrypted email capabilities for sensitive communications
Month 2: Strengthen and Test
- Implement regular backup procedures
- Conduct phishing simulation exercises
- Review and update access controls
Ongoing: Stay Vigilant
- Schedule quarterly security reviews
- Keep software and security measures updated
- Maintain regular employee training and awareness programs
The Bottom Line: Act Now, Before It's Too Late
Email security isn't just about technology: it's about protecting everything you've built. Your customer relationships, your reputation, your financial stability, and your ability to operate depend on keeping email threats at bay.
The question isn't whether you'll face an email-based attack. It's when. And when that moment comes, will you be prepared?
Don't wait until you're the next local business making headlines for all the wrong reasons. Take action today to protect your email systems, train your employees, and build the defenses your business needs.
Ready to secure your business email? Contact us at Preferred Computer Solutions for a free email security assessment. We'll work with you to identify vulnerabilities and create a customized protection plan that fits your budget and business needs. Because when it comes to your business security, you deserve a local partner you can trust.



Recent Comments